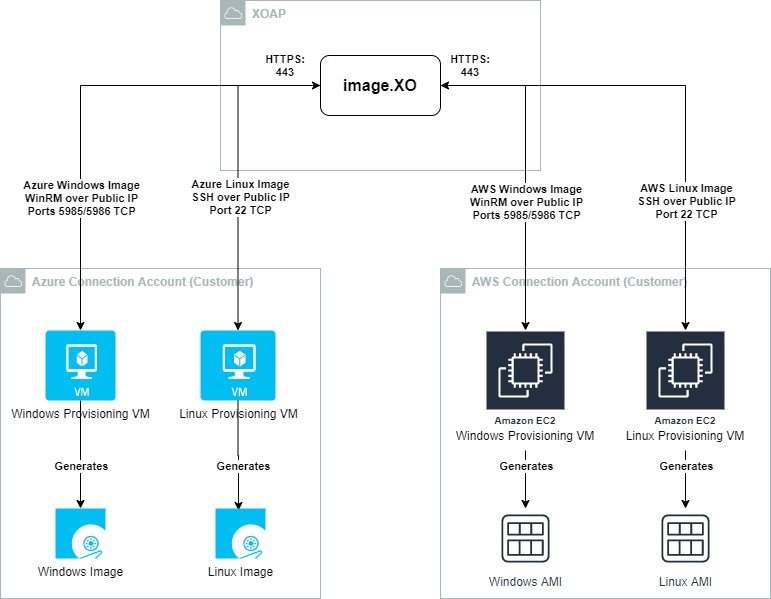
Communication diagram #
The following communication diagram explains the flow of communication for image.XO:
AWS #
Please have a look at the following prerequisites for the creation of images on AWS.
A default VPC should be available in the account were you want to create the customized image.
You should also assign IAM permissions to the user you are specifying for the connection with at least the following permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "NonResourceBasedReadOnlyPermissions",
"Action": [
"ec2:DescribeSubnets",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshots",
"ec2:DescribeImages",
"ec2:DescribeVolumes",
"ec2:DescribeInstances"
],
"Effect": "Allow",
"Resource": "*"
},
{
"Sid": "NonResourceBasedWritePermissions",
"Action": [
"ec2:CopyImage",
"ec2:CreateImage",
"ec2:CreateKeyPair",
"ec2:CreateSecurityGroup",
"ec2:CreateSnapshot",
"ec2:CreateTags",
"ec2:CreateVolume",
"ec2:DeleteKeypair",
"ec2:DeleteSnapshot",
"ec2:ModifyImageAttribute",
"ec2:ModifyInstanceAttribute",
"ec2:RegisterImage"
],
"Effect": "Allow",
"Resource": "*"
},
{
"Sid": "IAMPassroleToInstance",
"Action": [
"iam:PassRole"
],
"Effect": "Allow",
"Resource": "arn:aws:iam::_ACCOUNT_ID_:role/_ROLE_NAME_"
},
{
"Sid": "AllowInstanceActions",
"Effect": "Allow",
"Action": [
"ec2:AttachVolume",
"ec2:DetachVolume",
"ec2:StopInstances",
"ec2:TerminateInstances"
],
"Resource": "arn:aws:ec2:_REGION_:_ACCOUNT_ID_:instance/*",
"Condition": {
"StringEquals": {
"ec2:InstanceProfile": "arn:aws:iam::_ACCOUNT_ID_:instance-profile/_ROLE_NAME_"
}
}
},
{
"Sid": "EC2RunInstances",
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:_REGION_:_ACCOUNT_ID_:instance/*",
"Condition": {
"StringEquals": {
"ec2:InstanceProfile": "arn:aws:iam::_ACCOUNT_ID_:instance-profile/_ROLE_NAME_"
}
}
},
{
"Sid": "EC2LimitSize",
"Effect": "Deny",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:_REGION_:_ACCOUNT_ID_:instance/*",
"Condition": {
"ForAnyValue:StringNotLike": {
"ec2:InstanceType": [
"*.nano",
"*.small",
"*.micro"
]
}
}
},
{
"Sid": "EC2RunInstancesSubnet",
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:_REGION_:_ACCOUNT_ID_:subnet/*",
"Condition": {
"StringEquals": {
"ec2:Vpc": "arn:aws:ec2:_REGION_:_ACCOUNT_ID_:vpc/_VPC_ID_"
}
}
},
{
"Sid": "RemainingRunInstancePermissions",
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": [
"arn:aws:ec2:_REGION_:_ACCOUNT_ID_:volume/*",
"arn:aws:ec2:_REGION_::image/*",
"arn:aws:ec2:_REGION_::snapshot/*",
"arn:aws:ec2:_REGION_:_ACCOUNT_ID_:network-interface/*",
"arn:aws:ec2:_REGION_:_ACCOUNT_ID_:key-pair/*",
"arn:aws:ec2:_REGION_:_ACCOUNT_ID_:security-group/*",
"arn:aws:ec2:_REGION_:_ACCOUNT_ID_:subnet/*"
]
},
{
"Sid": "EC2VpcNonresourceSpecificActions",
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupIngress",
"ec2:DescribeSecurityGroups",
"ec2:DeleteSecurityGroup"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:Vpc": "arn:aws:ec2:_REGION_:_ACCOUNT_ID_:vpc/_VPC_ID_"
}
}
}
]
}You can read more about necessary permissions here.
Azure #
Please have a look at the following prerequisites for the creation of images on Azure.
Create a Service Principal with contributor role access to an Azure subscription with Azure CLI (Source).
Command format #
az ad sp create-for-rbac --name [ServicePrincipalName] --role Contributor --scopes /subscriptions/[SubscriptionId] --years 1Command example #
az ad sp create-for-rbac --name xoap-image-principal --role Contributor --scopes /subscriptions/xxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx --years 1Command output #
{
"appId": "[ClientId (Guid)]",
"displayName": "xoap-image-principal",
"name": "http://xoap-image-principal ",
"password": "[Password/ClientSecret]",
"tenant": "[TenantId (Guid)]"
}From that output, you can create a connection for your subscription.
SubscriptionId: xxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
TenantId (tenant): [Guid]
ClientId (appId): [Guid]
ClientSecret (password) [Text]


