Table of contents
Implementing STIG compliance in your organization makes perfect sense. STIG (Security Technical Implementation Guide) is a set of security configuration standards and guidelines created by the DISA (Defense Information Systems Agency) to improve the security of DoD systems and data.
Moreover, STIGs are used to make sure that information systems are configured securely, in a standardized manner and that they comply with DoD policies and security best practices.
Today, we’ll guide you through a simple STIG implementation using XOAP automation platform. Let’s get started! 🛡️
Avoid these STIG challenges with XOAP
Complexity, cost, frequent updates
Implementing STIGs comes with several challenges. Firstly, the detailed and comprehensive nature of STIGs can make it difficult to understand and implement all requirements correctly.
Secondly, implementing STIGs can be resource-intensive, requiring significant time, effort and expertise. Organizations may need specialized personnel to interpret and apply the guidelines correctly.
Furthermore, STIGs are frequently updated to address new vulnerabilities and evolving security threats. Keeping up with these updates and ensuring that systems remain compliant can be challenging for many organizations.
Interoperability issues, downtime, inspections
Applying STIGs can lead to compatibility or interoperability issues, especially in complex environments with a mix of newer and older systems or different operating systems and applications. Moreover, the implementation of STIGs can have operational impacts, such as system downtime or reduced performance, as configurations are changed and tested for compliance.
Lastly, maintaining thorough documentation to demonstrate compliance with STIG requirements can be burdensome. Organizations must be prepared for audits and inspections to verify compliance.
Despite these challenges, the implementation of STIGs is crucial for maintaining high-security standards within DoD systems and minimizing the risk of cyber attacks and vulnerabilities. And with the help of XOAP’s security standards compliance, it doesn’t have to be so complicated.
Achieve STIG security compliance in a few steps
To help you with the implementation of the STIG we’re regularly releasing STIG DSC modules on GitHub. You can use these modules to deploy STIG on your infrastructure. The easiest way to do that is to use our Configuration Management.
If you’re new to XOAP, you can create your free account. Once your account is created, use our DSC Configuration Wizard to create your STIG DSC configuration.
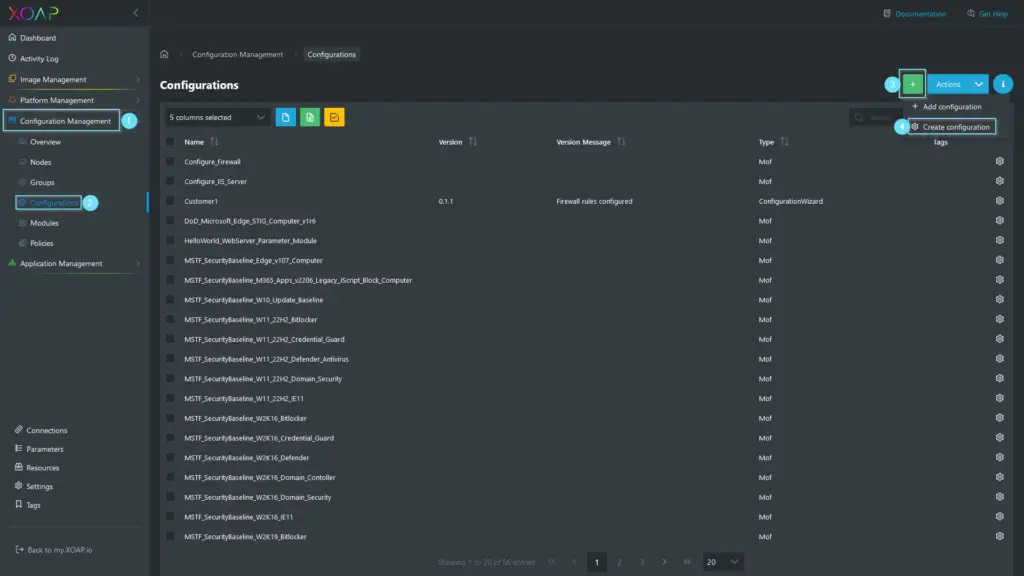
Navigate to Configuration Management > Configurations and click the green + to create a new configuration.
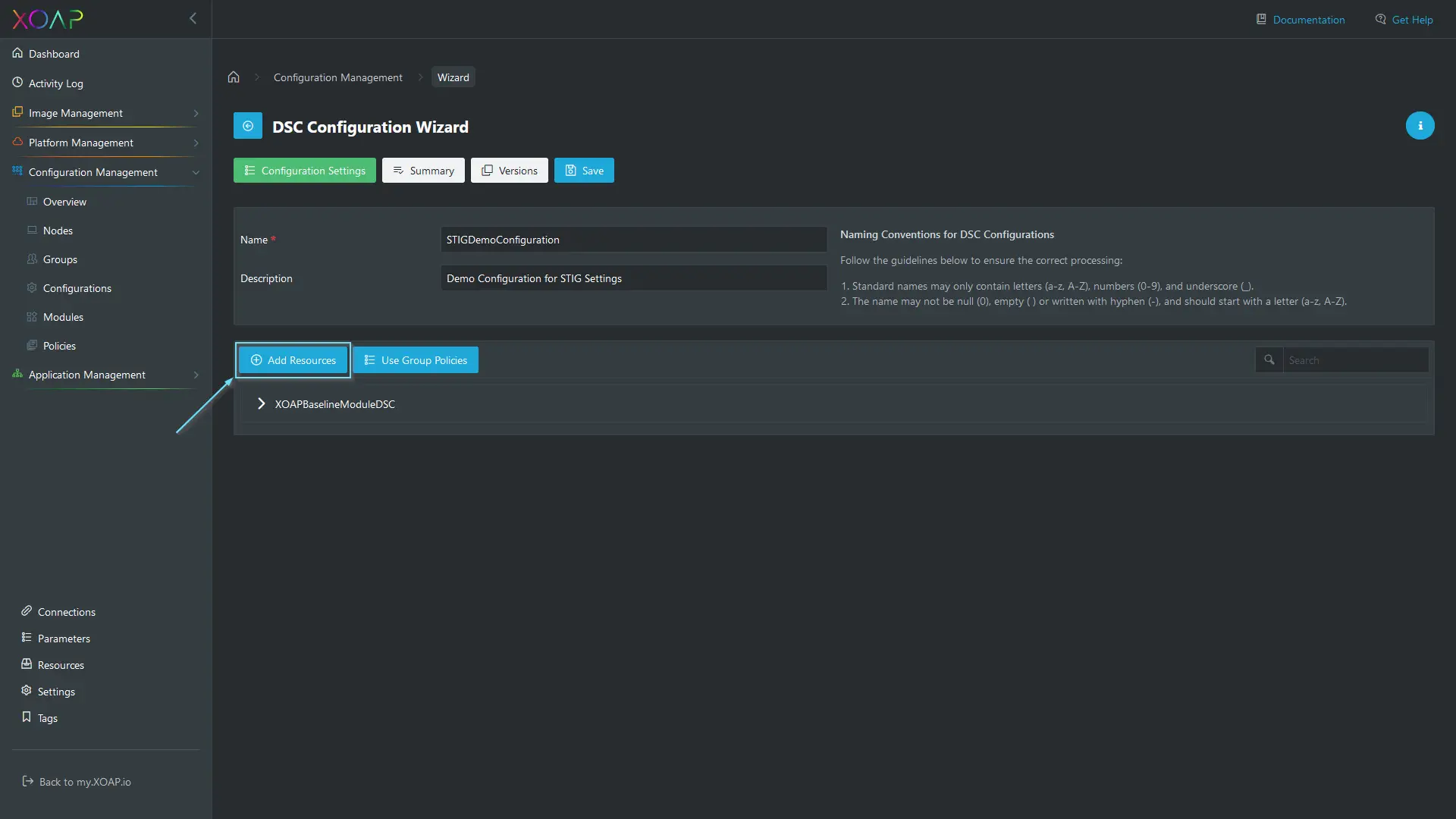
In the DSC Configuration wizard, specify a name and a description for your configuration. After that click “Add Resources” to add STIG resources.
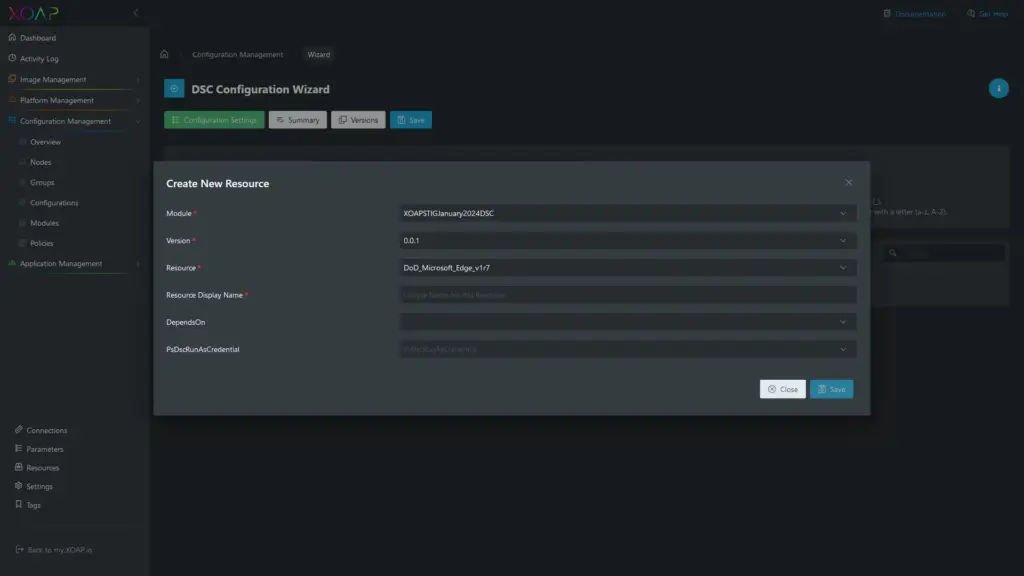
In the “Create New Resource” window select the STIG module you want to use, the module version and the specific resource which you want to apply. The resources are named according to their use case. The only thing you need to provide is the Resource Display Name.
⚠️ Resource names must be unique within a DSC configuration!
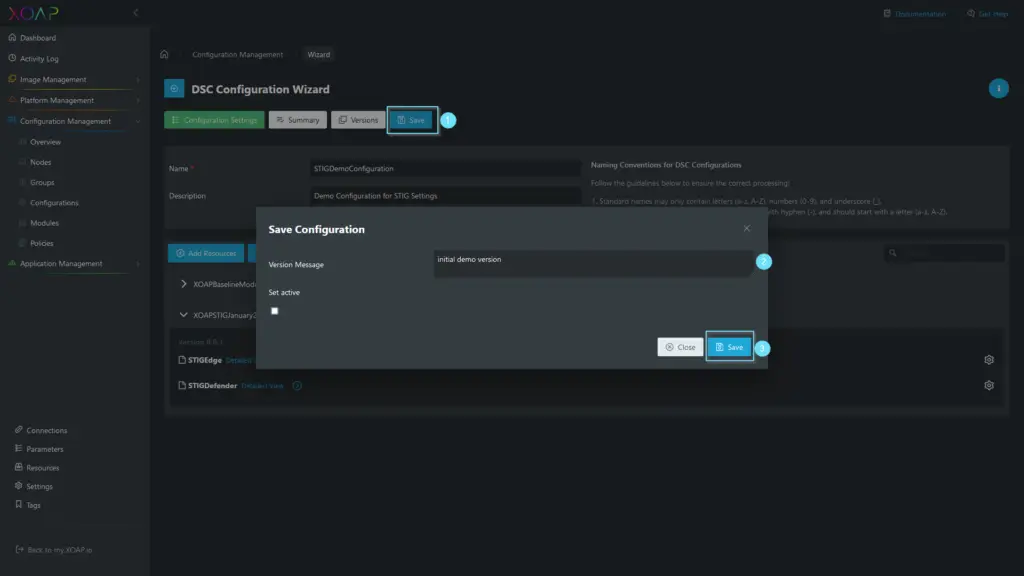
Once you are ready with adding resources click “Save” in the “Create New Resource” window. If you need to add more resources, repeat the same steps for all needed resources. To create the configuration, click “Save” in DSC Configuration Wizard, provide a “Version Message” in the “Save Configuration” window and click Save.
Saving the configuration will start a background job that compiles the configuration. In approximately 10 to 15 minutes, your configuration will be ready. While waiting we can create a new group that this configuration will be assigned to.
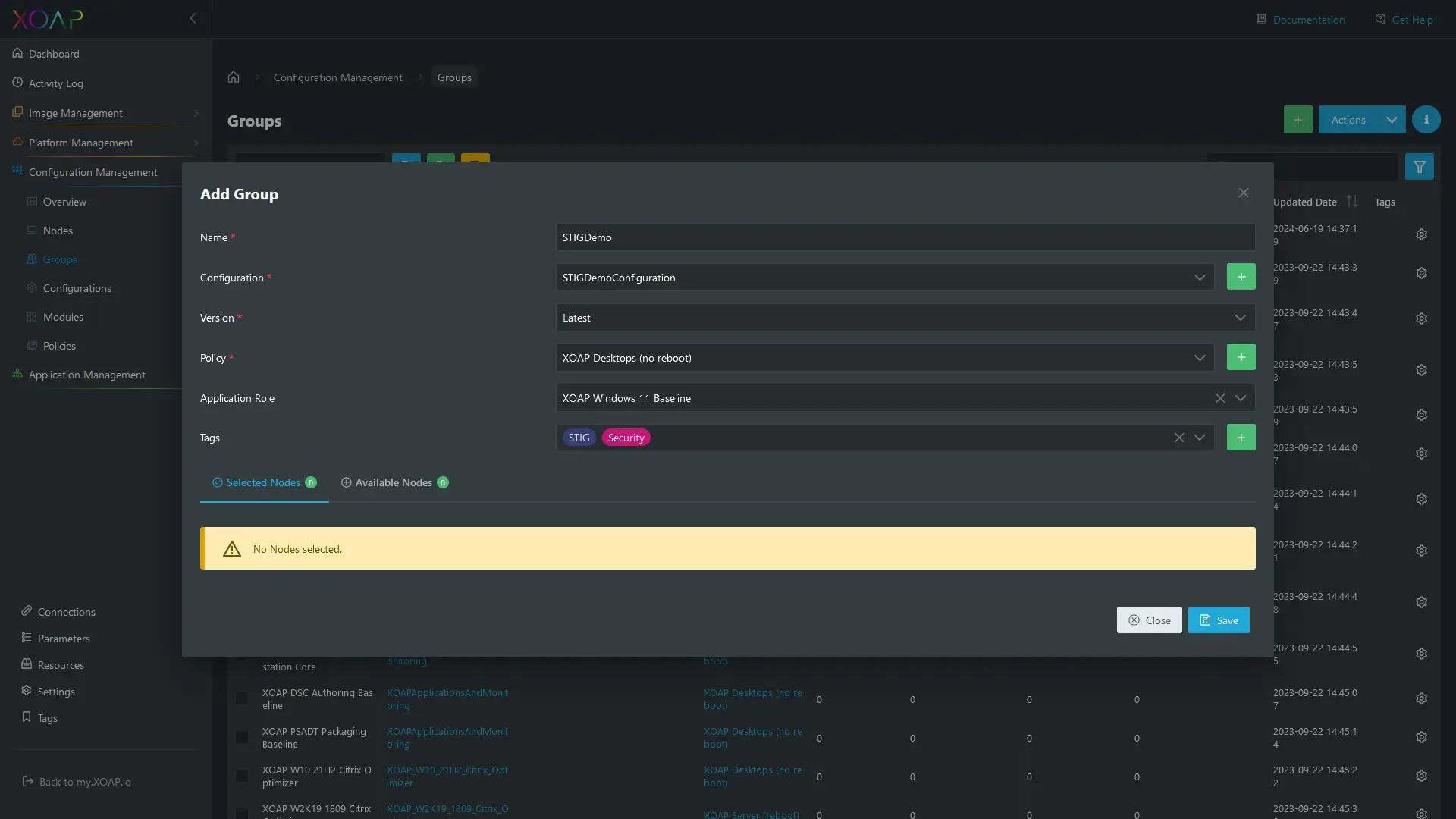
To create a new group, go to Configuration Management > Groups and click the green + button. In the “Add Group” window provide a name, select the saved Configuration with the desired version and choose a policy. If you want, you can assign an Application Role (from the Application Management module) and provide Tags as needed.
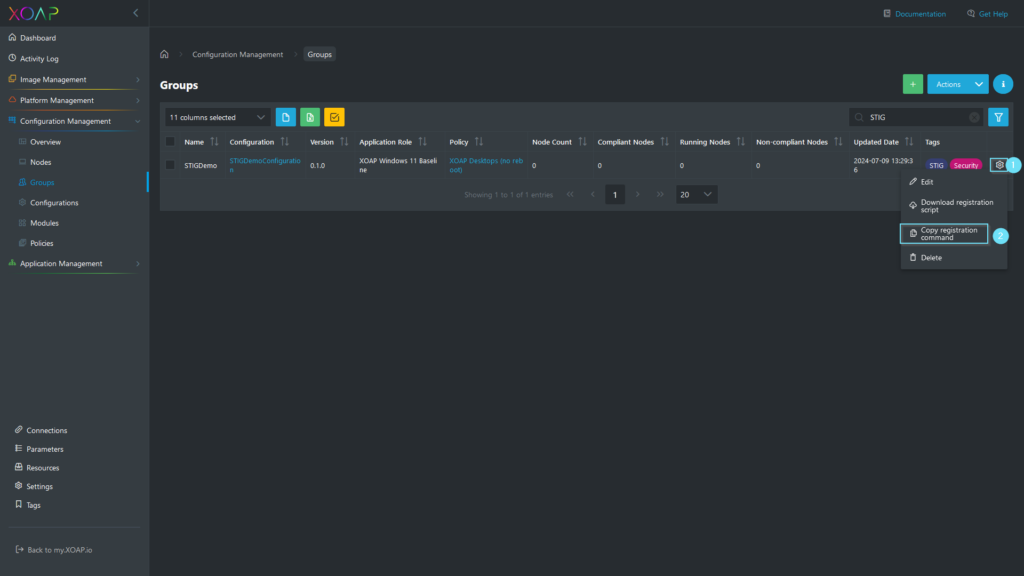
When you are ready, click save in “Add Group” window. To register a node in XOAP and to automatically apply the created STIG configuration to the node, find the group in the Groups table, click on the action menu and select “Copy registration command”.
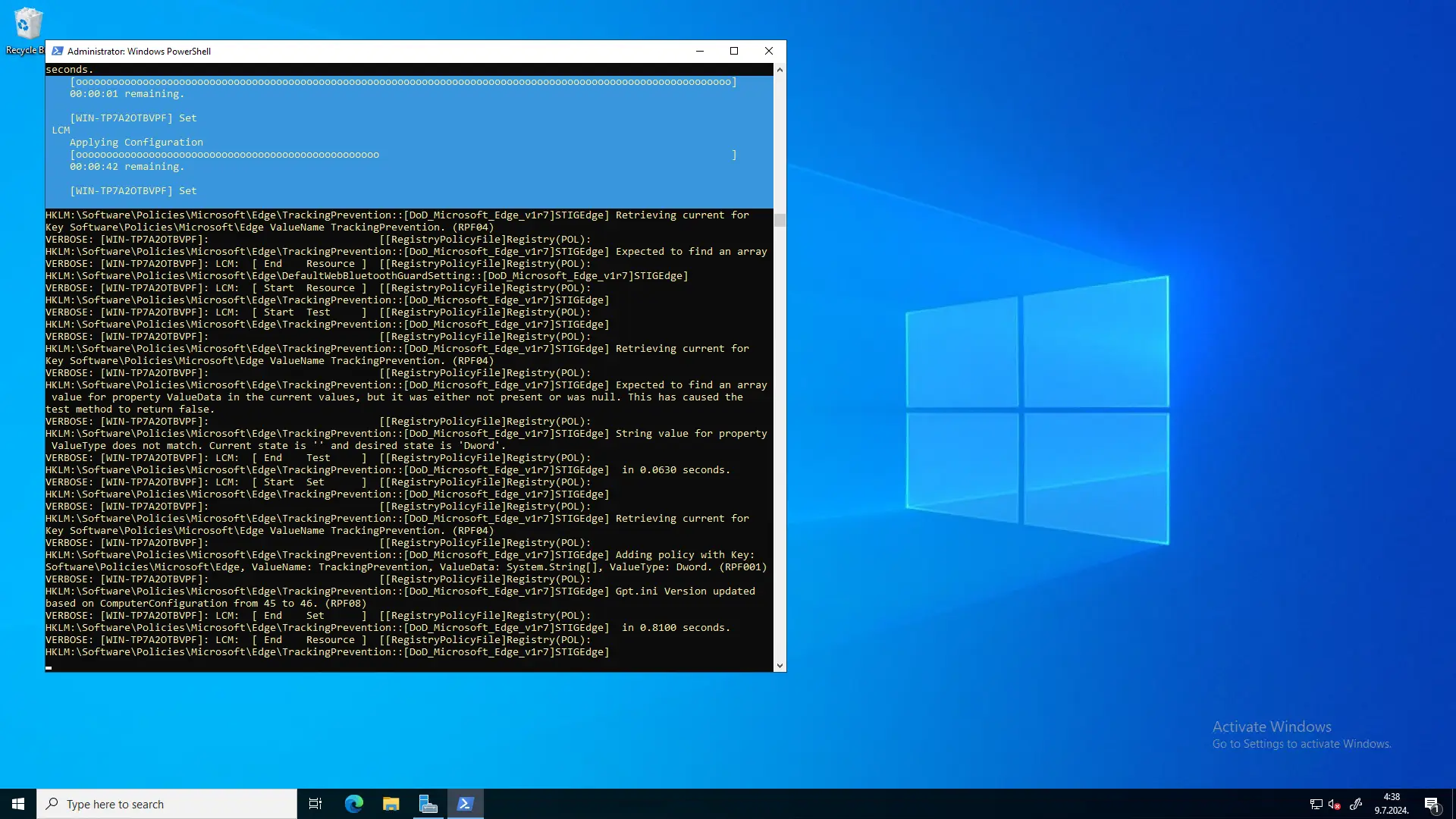
This will copy the necessary registration command into your clipboard. The next step is to go on your Node, run Windows PowerShell as administrator, and paste and run the command.
After running the command, the configuration will be downloaded and applied:
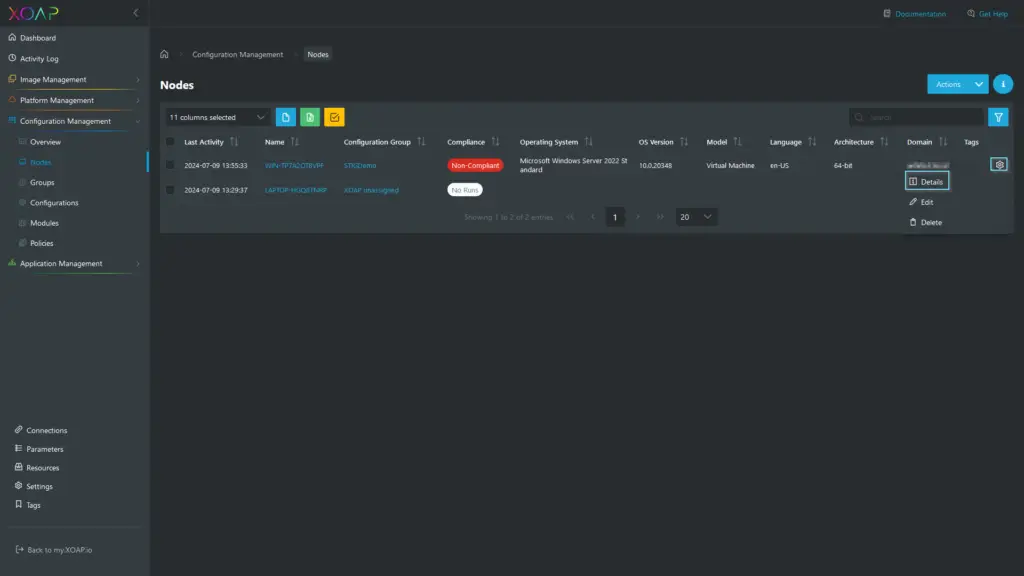
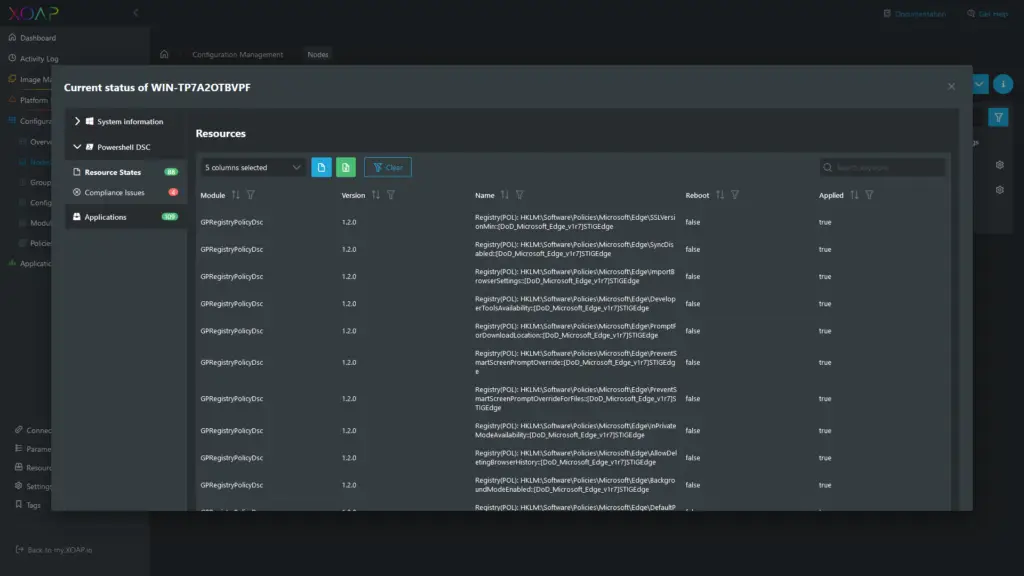
Once finished your Node will be visible in the Nodes area in Configuration management. In case of any problems, you can easily detect which configuration item is the reason, and which specific configuration is not compliant.
To get that information, go to Configuration Management > Nodes, find your Node, click the “Action Menu” and select “Details”.
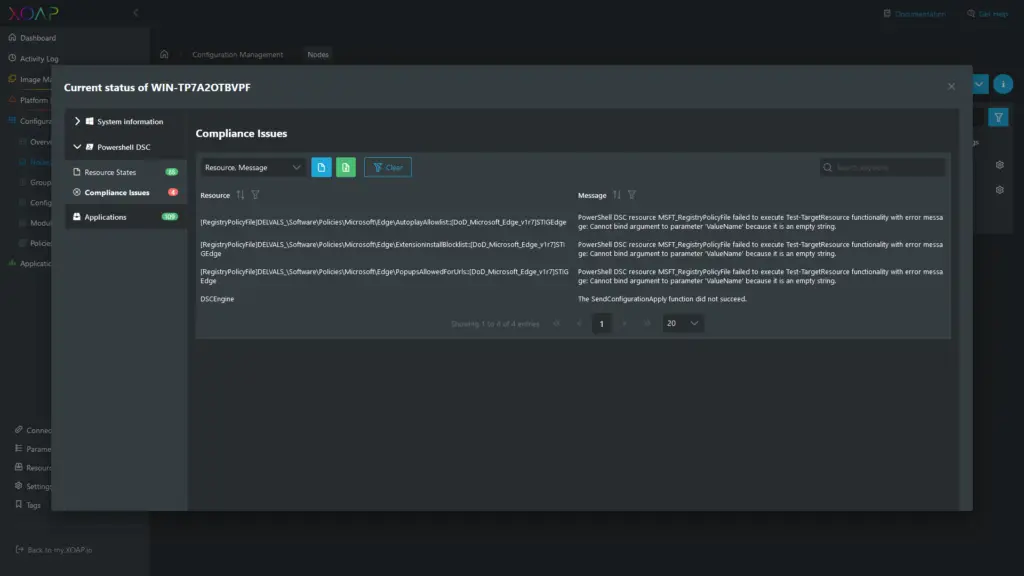
In the “Current Status” window, in the PowerShell DSC menu, you can find information about successfully applied configurations, and resources within the configuration that are causing issues:
Compliance issues show you details about resources that could not be applied or that caused issues. From here on you can see which resources need to be adjusted to get a compliant state.
As many settings of the STIG recommendations can cause issues depending on the environment, you can simply download the module and adjust it to your own needs. After adjustments, upload it again and reapply it with another configuration version as described above.
💡 STIG implementation: The simple way
Applying STIGs in only a few steps simplifies the deployment of secure systems without the need for complex infrastructures or procedures. With XOAP, you have one central console to configure the security configurations, check the compliance state of your connected nodes and to deploy further updates when needed.
As we regularly provide new STIG DSC modules on GitHub, you can always upload the latest available ones to your workspace and use the same procedure as described above to apply the newest STIG security settings.
If you need additional help getting started with applying STIG book a free 30-min demo. 👋