Table of contents
Modern endpoint management with Microsoft Intune enables IT teams to automate device provisioning and management processes, including Windows Autopilot scenarios and Hybrid Azure AD Join.
However, not every organization operates in a greenfield environment.
Legacy infrastructures, often found in healthcare, public sector, education or manufacturing come with specific challenges:
- No Application Control features in firewalls
- No Host-based Ruleset automation
- No wildcard support for FQDN-based rules
- Manual IP address maintenance is required
This blog post outlines how to design a secure and operationally manageable firewall configuration for the Intune Connector for Active Directory, even in restricted and technically outdated environments.
The challenge
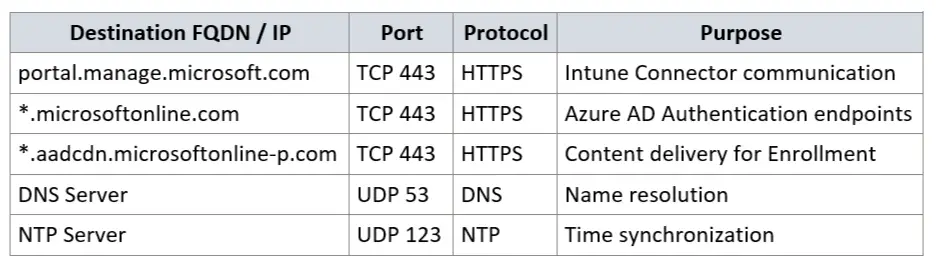
The Intune Connector for Active Directory requires outbound communication to various Microsoft cloud services to function properly. However, in legacy environments, this can present some challenges:
- No wildcard support in the firewall (no *.microsoft.com)
- No Application Control feature available
- Only specific IP addresses or FQDNs can be configured
- Firewall rules must be maintained manually
Recommended technical approach
Step 1: Identify required endpoints
Microsoft provides official documentation listing all required URLs and IP address ranges for Microsoft 365 services and Intune:
Focus Categories for Intune Connector:
- Microsoft 365 Common & Office Online
- Intune
- Azure Active Directory
Optional for Automation: Microsoft’s Endpoint API provides a machine-readable JSON file for automated processing (more here).
Step 2: Firewall ruleset design
Define dedicated outbound rules for the Intune Connector server.
Note: If DNS resolution is restricted, IP addresses must be resolved manually and configured explicitly in the firewall.
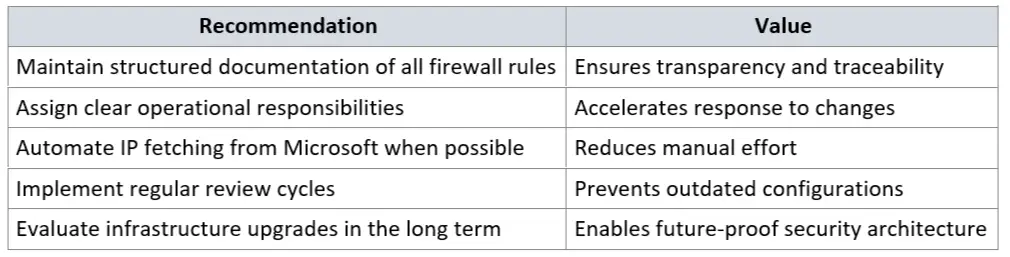
Step 3: Operational process for IP maintenance
Since Microsoft services evolve continuously, it’s essential to establish a reliable process for maintaining firewall rules.
Recommended steps:
- Monthly check of the official Microsoft documentation.
- Optional: PowerShell script querying the Microsoft Endpoint API for changes.
- Generate an automated notification or create a ticket for the firewall team.
- Keep documentation updated with the current IP ranges and URLs.
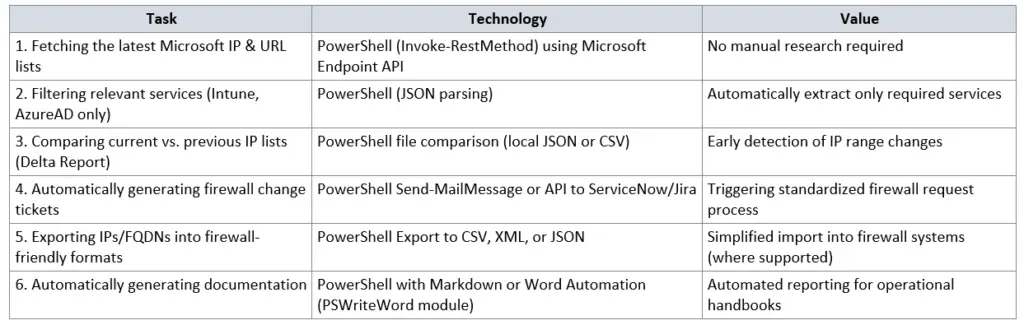
Step 4: Automation pipeline flow
- Update IP Addresses: Automated PowerShell script pulls the latest Microsoft Endpoint API data.
- Update DSC Config: IP addresses are dynamically injected into the DSC configuration template.
- XOAP Deploy: XOAP pulls the new configuration and applies it to the target firewall servers.
- Compliance check: XOAP runs a configuration compliance scan to validate correct deployment.
Read more about automated firewall changes with XOAP below ↓
Best practices for firewall management in legacy environments
Long-term optimization options
Organizations should evaluate possible optimizations over time:
- Upgrade firewall systems to support Application Control features.
- Implement transparent or explicit proxy solutions.
- Utilize Microsoft Azure Service Tags for dynamic IP management.
- Consider Azure Firewall or modern next-generation firewalls for cloud-centric environments.
Automation use cases
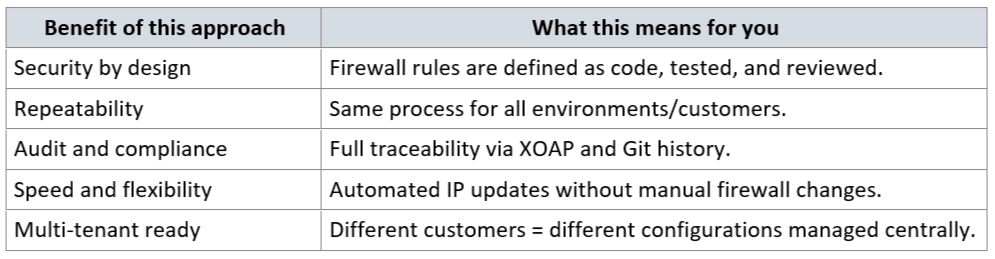
Fully automated firewall changes with XOAP's Configuration Management
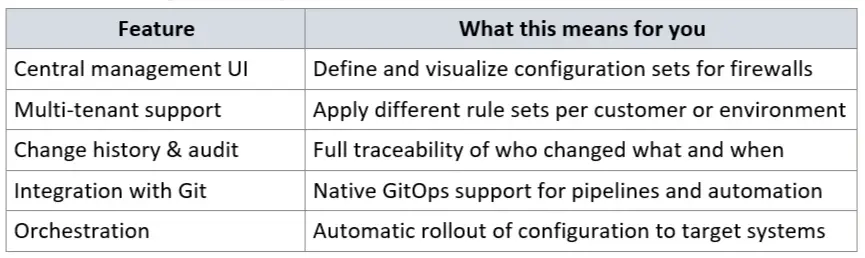
XOAP’s Configuration Management makes it easy to define, version and automatically deploy configuration settings across systems, including firewalls, servers, and other infrastructure components.
By using Config as Code principles alongside PowerShell Desired State Configuration (DSC), firewall rules can be fully automated, audited, and enforced across multiple environments.
XOAP integration provides:
Related: Automate firewall changes with XOAP
Final thoughts
Running Intune Connector for Active Directory in environments with strict firewall rules is possible. It just takes the right setup and processes. By creating clear firewall rules, managing IPs and keeping good documentation, even older systems can safely connect to Microsoft cloud services.