Table of contents
Picture this: It’s 4:30 PM on a Friday, and instead of winding down for the weekend, your team is scrambling. A security audit is looming, compliance reports are scattered across spreadsheets and a missed vulnerability now means potential fines and a late-night emergency fix. Stress levels are high, and the weekend? Canceled.
Now, we don’t want that, do we?
Failing to automate security compliance isn’t just inefficient—it’s a ticking time bomb. Security gaps widen, audits become nightmares and fines escalate quickly.
While security is never simple nor trivial, it can be streamlined, well covered and run like clockwork. Not every company has this control. Maybe you’ve seen some of them in the news.
If you’re considering security compliance automation for your IT environment, you know it’ll reduce costs, cut human error and provide system consistency. But where do you start? Specifically, with automating CIS, STIG and, if you’re operating in Germany like us, BSI.
Why automate CIS, STIG and BSI?
CIS, STIG and BSI are critical frameworks for robust security and protecting your systems from real threats. Maintaining them manually? It’s complex, time-consuming and prone to errors due to the sheer monumentality of the task. While CIS is a must, STIG and BSI might not be directly relevant to your organization. We suggest implementing them anyway.
CIS (Center for Internet Security) benchmarks provide global best practices for securing IT systems, covering everything from operating systems to cloud environments. They help minimize vulnerabilities and harden configurations, ensuring systems meet industry security standards. Automating CIS compliance gives you continuous security controls, real-time monitoring and quick remediation, boosting your overall security with less manual effort.
For businesses working with U.S. federal agencies or defense contractors, STIG (Security Technical Implementation Guidelines) compliance is mandatory. Even if you don’t have a direct connection to the U.S., implementing STIG is a smart move as it provides strict security configurations for systems. Given its notorious complexity when enforced manually, automating STIG implementation helps you stay compliant without getting bogged down in tedious configurations.
If you’re based in Germany, you already know that BSI (Bundesamt für Sicherheit in der Informationstechnik) compliance is crucial. When BSI is automated, security measures are consistently applied and updated, reducing the risk of non-compliance penalties. But there’s a second benefit to implementing BSI for those operating in or with critical sectors of the European Union—BSI compliance sets you up for the strict and comprehensive EU-wide NIS2 cybersecurity requirements, covering many of the same areas. >> More on NIS2 automation
Source: Freepik
Challenges of automating across different systems
While automation can be the deciding factor when it comes to security, automating across different systems comes with its own set of challenges. And there are plenty. You may have a mix of legacy infrastructure, cloud environments, on-premise systems and third-party tools in your infrastructure. Each of these systems has its own quirks, configurations and security requirements, making integration tricky.
Legacy systems are often rigid, outdated and weren’t built for automation. This makes introducing modern automated compliance tough and leads to compatibility issues, gaps in coverage and even unexpected downtime.
Then, there’s the fact that different systems often use different security protocols and tools. You might be running one system with a firewall solution that’s highly specific to your environment, while another is using a cloud-native solution with its own security framework. Ensuring compatibility between these security controls often requires custom configurations and careful coordination.
Another challenge comes when systems are highly customized or rely on vendor-specific tools. In this case, automation tools might need to be fine-tuned—or even completely reworked—to adapt. Vendor lock-in can complicate matters even more, as you’re limited by the functionality and flexibility of your chosen solution.
Automation also relies heavily on effective cross-system communication. To ensure that all systems are in sync, especially when patching vulnerabilities, monitoring compliance and generating reports, your systems need to “talk” to each other. If there are mismatched data formats or integration barriers, this can cause automation workflows to break down and require manual intervention.
Finally, as your organization grows, so do your automation needs. What worked for a small environment might need adjustments as your infrastructure scales. It’s crucial to have flexible, scalable automation to manage evolving infrastructure and compliance demands.
How to handle all this
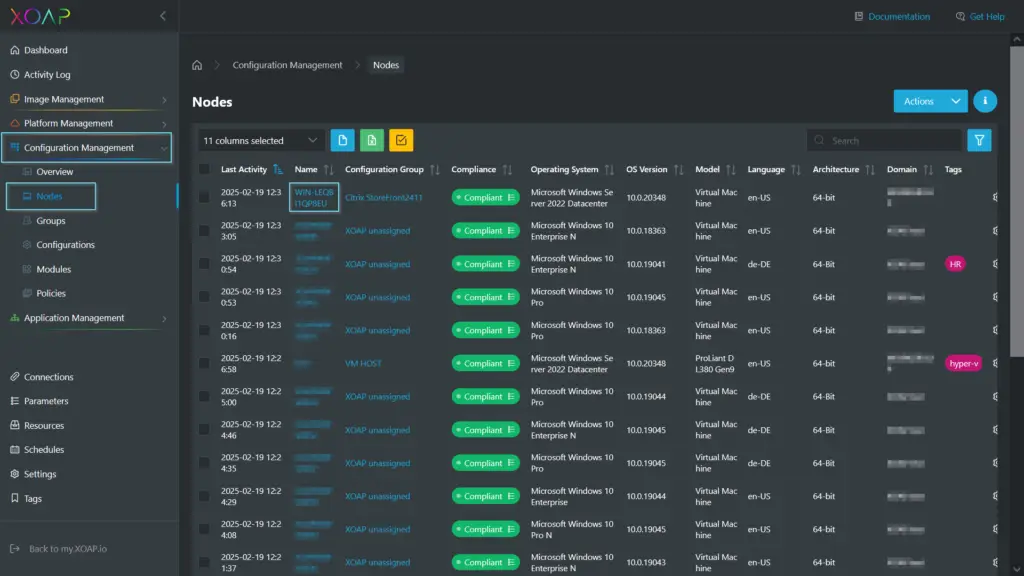
If this seems a bit daunting, that’s because it is. From legacy infrastructure to cloud environments, the complexities involved in automating compliance across different systems can be a lot. There is a solution, though. We designed XOAP to solve these exact challenges and make security compliance automation smooth, scalable and reliable. On top of automating anything in your IT infrastructure, XOAP takes the headache out of managing STIG, CIS and BSI compliance—all from a single, unified platform.
XOAP seamlessly integrates with various systems, whether legacy or cloud, maintaining consistent security policies with minimal manual effort. Even if your setup is highly customized or uses vendor-specific tools, XOAP adapts without the need for major adjustments. No vendor lock-ins, just flexible automation that fits your needs.
What really sets XOAP apart is its real-time monitoring and automated remediation. When a vulnerability is detected, XOAP not only flags it but also applies the necessary fix, keeping your systems compliant and reducing downtime. It also solves the problem of cross-system communication, eliminating integration barriers and making sure that patch management and vulnerability assessments run smoothly across all your systems.
As your business grows, XOAP scales with the evolving infrastructure, ensuring that the compliance processes stay up to date and efficient as your needs change.
Automating STIG, CIS and BSI compliance this way becomes straightforward, leaving you free to focus on your business while XOAP takes care of the security details.
And those security audits? With XOAP’s automated reports, your only worry will be picking the report cover.
📚 More on security automation:
>> Achieving up to 98% CIS compliance
>> STIG security across all systems
>> Security compliance made easy
>> Why XOAP
Still not sure about automating your IT security? Let’s talk! You can book a timeslot below. If you’d like to explore XOAP yourself, start with a free account.