Table des matières
La gestion moderne des terminaux avec Microsoft Intune permet aux équipes informatiques d'automatiser les processus de provisionnement et de gestion des appareils., y compris Scénarios Windows Autopilot et Hybrid Azure AD Join.
Cependant, toutes les organisations n'opèrent pas dans un environnement entièrement nouveau.
Infrastructures existantes, souvent dans les soins de santé, le secteur public, l'éducation ou l'industrie manufacturière s'accompagnent de défis spécifiques :
- Pas de fonctions de contrôle des applications dans les pare-feux
- Pas d'automatisation des jeux de règles basés sur l'hôte
- Pas de prise en charge des caractères génériques pour les règles basées sur les FQDN
- Une mise à jour manuelle de l'adresse IP est nécessaire
Cet article de blog présente comment concevoir une configuration de pare-feu sûre et gérable sur le plan opérationnel pour le connecteur Intune pour Active Directory, même dans des environnements restreints et techniquement dépassés.
Le défi
Pour fonctionner correctement, le connecteur Intune pour Active Directory a besoin d'une communication sortante avec divers services Microsoft en nuage. Cependant, dans les environnements existants, cela peut poser quelques problèmes :
- Pas de prise en charge des caractères génériques dans le pare-feu (pas de *.microsoft.com)
- Aucune fonction de contrôle des applications n'est disponible
- Seules des adresses IP ou des FQDN spécifiques peuvent être configurées.
- Les règles du pare-feu doivent être gérées manuellement
Approche technique recommandée
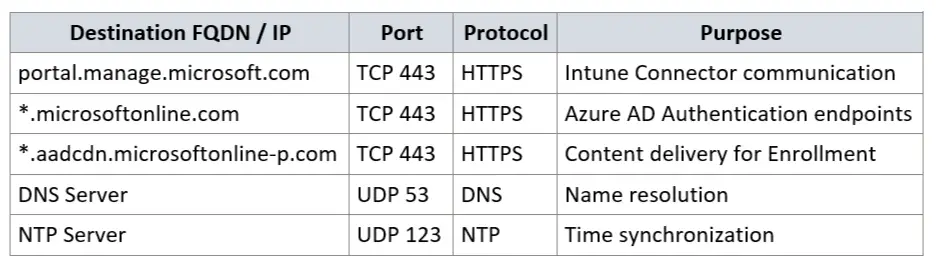
Étape 1 : Identifier les points de terminaison nécessaires
Microsoft fournit documentation officielle la liste de toutes les URL et plages d'adresses IP requises pour les services Microsoft 365 et Intune :
Catégories d'intérêt pour Intune Connector :
- Microsoft 365 Common & Office Online
- Intune
- Azure Active Directory
Facultatif pour l'automatisation : L'API Endpoint de Microsoft fournit un fichier JSON lisible par une machine pour un traitement automatisé (plus ici).
Étape 2 : Conception du jeu de règles du pare-feu
Définir des règles de sortie dédiées au serveur Intune Connector.
Remarque : Si la résolution DNS est restreinte, les adresses IP doivent être résolues manuellement et configurées explicitement dans le pare-feu.
Étape 3 : Processus opérationnel pour la maintenance de la propriété intellectuelle
Les services Microsoft évoluant en permanence, il est essentiel d'établir un processus fiable pour la mise à jour des règles de pare-feu.
Mesures recommandées :
- Vérification mensuelle de la documentation officielle de Microsoft.
- Facultatif : Script PowerShell interrogeant l'API Microsoft Endpoint pour les changements.
- Générer une notification automatique ou créer un ticket pour l'équipe du pare-feu.
- Maintenir la documentation à jour avec les plages d'adresses IP et les URL actuelles.
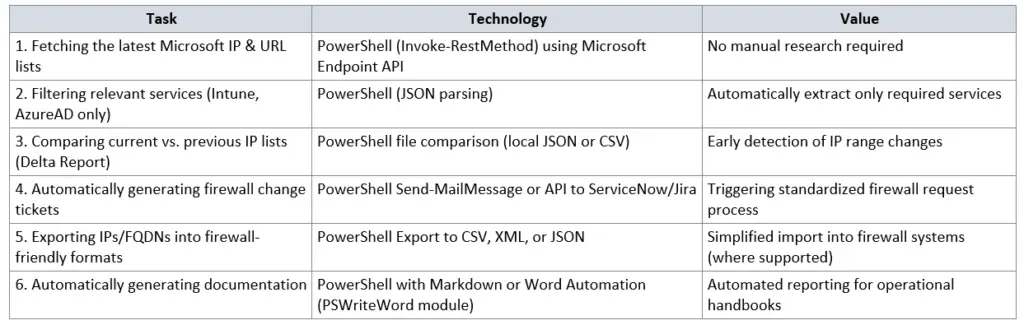
Étape 4 : Flux du pipeline d'automatisation
- Mettre à jour les adresses IP : Un script PowerShell automatisé extrait les dernières données de l'API Microsoft Endpoint.
- Mettre à jour la configuration DSC : Les adresses IP sont injectées dynamiquement dans le modèle de configuration du DSC.
- XOAP Deploy : XOAP récupère la nouvelle configuration et l'applique aux serveurs de pare-feu cibles.
- Contrôle de conformité : XOAP effectue une analyse de conformité de la configuration pour valider le déploiement correct.
En savoir plus modifications automatisées du pare-feu avec XOAP ci-dessous ↓
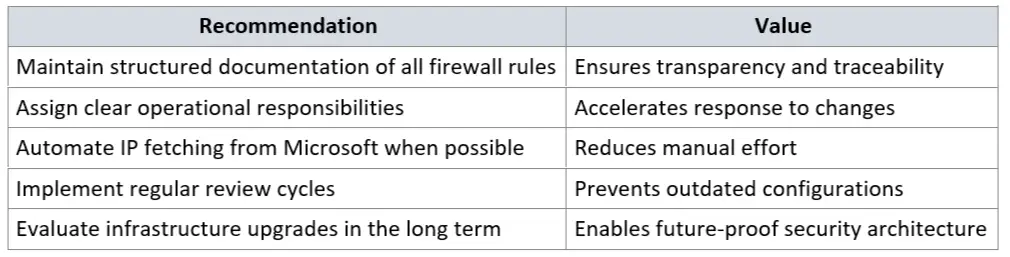
Meilleures pratiques pour la gestion des pare-feux dans les environnements existants
Options d'optimisation à long terme
Les organisations devraient évaluer les optimisations possibles au fil du temps :
- Mettre à jour les systèmes de pare-feu pour qu'ils prennent en charge les fonctions de contrôle des applications.
- Mettre en œuvre des solutions de proxy transparentes ou explicites.
- Utilisez les balises de service Microsoft Azure pour la gestion dynamique des adresses IP.
- Pensez à Azure Firewall ou à des pare-feu modernes de nouvelle génération pour les environnements centrés sur le cloud.
Cas d'utilisation de l'automatisation
Changements de pare-feu entièrement automatisés avec Configuration Management de XOAP
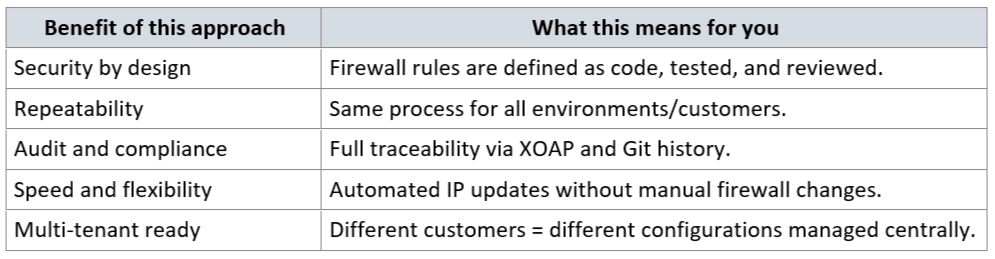
XOAP's Configuration Management facilite la définition, la version et le déploiement automatique des paramètres de configuration dans les systèmes, y compris les pare-feu, les serveurs et les autres composants de l'infrastructure.
En utilisant les principes de Config as Code avec PowerShell Desired State Configuration (DSC), les règles de pare-feu peuvent être entièrement automatisées, auditées et appliquées dans plusieurs environnements.
L'intégration de XOAP fournit :
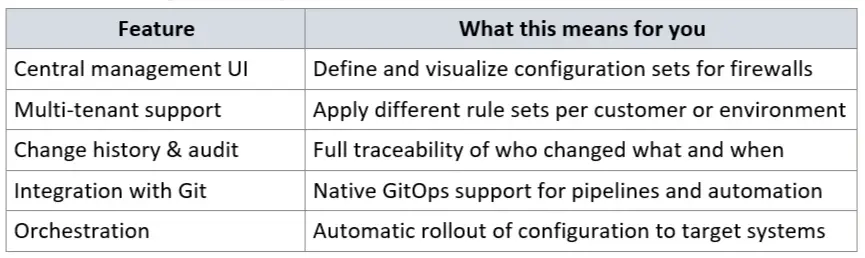
En rapport : Automatiser les changements de pare-feu avec XOAP
Dernières réflexions
Il est possible d'exécuter Intune Connector for Active Directory dans des environnements soumis à des règles de pare-feu strictes. Il suffit d'adopter la bonne configuration et les bons processus. En créant des règles de pare-feu claires, en gérant les IP et en conservant une bonne documentation, même les systèmes plus anciens peuvent se connecter en toute sécurité aux services en nuage de Microsoft.